The number of attacks on ATMs increases every year.

The number of attacks on ATMs increases every year. The attacks themselves are changing, becoming more complex and sophisticated. Moreover, if several years ago bank clients were the main target for hackers, the criminals were hunting for bank card data and account information, now they have turned their attention to financial institutions. Obviously, you can steal much more from a bank than from any of its clients — here we are talking about millions of euros.
For a long time, all attacks using special equipment or software were called logical. However, there are so many types of these attacks, so banking technology security specialists have even identified a separate group of terminal related fraud attacks. That is about skimming, shimming and trapping. In 2018 the number of terminal related fraud attacks decreased by 36% compared to 2017, but the total amount of stolen money remains huge: 247 million euros in 2018 and 353 million in 2017 (according to European Association of Secure Transactions, EAST).
Skimming and shimming – which one is more dangerous?
Skimming has always been popular. Today criminals can buy skimmers online and they are cheap. It takes a minute to install and remove it, and doesn‘t cause any suspicion from the bank security service.
So what are skimming devices? They are devices meant to look like original ATM components (card readers, keyboards, video cameras, ATM front panels) that steal data from a magnetic strip of a card and the pin code during a transaction. The stolen data is then recorded on a new magnetic strip, which they glue onto fake cards to later use for fraud. With this card, they can cash out money at any ATM.
Today banks use different ways to reduce their losses from skimming. They install anti-skimming devices on ATMs, which protect ATMs from skimmer installation. Unfortunately, criminals quickly learn how to cheat these defenses. Another way to protect your customers is to install special software which analyzes the behavior of the cardholder and blocks the card in case of suspicious actions. However, most of these solutions do not take into account a number of factors. This often leads to unreasonable blocking, for example, when using a card abroad.
Today the best strategy, according to experts, is to use comprehensive protection. It means to install a special device on ATM that creates electromagnetic interference to obstruct unauthorized data recording from the cards magnetic strips, and to install fraud control systems with complex analytical algorithms that work with large amounts of data.
Just a few years ago, experts advised to use cards with EMV-chips, because it was impossible to fake them. However, criminal ways are becoming increasingly technical with a constant battle for innovation on both fronts. Today, criminals can steal data even from a chip card. This is called shimming and they use special shimming devices for this.
A special device called “shimmer” is inserted into the ATM card slot. This is a thin microprocessor board that records chip data during a transaction. It is even more difficult to detect a shimmer than a skimmer, because it fits inside the card reader and is invisible to the ATM user. Users can suspect that there is something inside, only if the card is tight enough in the slot.
It‘s still impossible for criminals to make a new chip with stolen data, but they can record this data on a magnetic strip. Shimming is gaining popularity, but criminals will not be able to use the stolen data if two-factor authentication is required to confirm the transaction. Unfortunately, many issuers neglect this standard.
Another way of terminal fraud is ATM trapping. It can be divided into 2 types: grabbing a card from a card reader (card-trapping) and grabbing cash during cash-out (cash-trapping) using a special loop trap. In the last few years, trapping has lost its former popularity: it requires a lot of effort and does not give much return.
Modern systems of video monitoring and fraud prevention can protect ATMs from installing skimmers, shimmers and other devices. They can record video during any interaction with a terminal, react to the sticking of the camera, and notify the security service in any suspicious situation.
Social engineering and the human factor
As noted above, one of the main trends of recent years is that hackers have shifted their attention from end-users to financial institutions. Having access to the banking system, hackers can snatch much more money, while catching them is becoming more difficult. It‘s enough to gain access to the computer of a bank employee, from there the way to the internal systems is open, including the terminal networks.
The most popular way to do it is to send e-mail. The hackers do it on behalf of the client of the bank, the Central Bank or government agencies. As soon as a bank employee opens a document from this letter, malware intrudes in a computer system and immediately begins to spread through the internal network of the financial organization.
This way criminals find the computer with access to the terminals network and upload malware on to ATMs through it. The infected ATM computer sends a command to the dispenser to issue all the money, but these changes are not reflected in the internal IT system of the bank, the bank still thinks that the ATM is full of cash. Then the program deletes itself. It is very difficult to track such malware. Many banks do not report these attacks because of fear of reputational losses.
Another way to gain access to the internal IT system of a bank is to use bank employee data, accidentally or intentionally provided to attackers. So, employee access management and implementing multi-factor authentication can solve these problems.
How to protect ATMs from attacks
To not be afraid of logical and terminal related attacks banks must be one step ahead of criminals. Unfortunately, some financial organizations are still not paying enough attention to the security of their terminal equipment, do not update ATM software regularly, and do not ensure proper configuration of the internal networks.
Only a comprehensive approach can fix vulnerabilities in the ATM security infrastructure. Modern solutions for video surveillance and fraud prevention will reduce the risk of physical attacks and logical terminal related fraud attacks (skimming, shimming, trapping). At the same time, the terminal network will be protected from attacks through the banking infrastructure.
BS/2, in cooperation with the technology solutions for banks and retail supplier, Diebold Nixdorf, offer an integrated approach to ATM security. It includes ATMeye.iQ - a solution for video surveillance and fraud prevention, and Vynamic Security - a solution to protect the ATM fleet from any kind of intrusion and fraud.
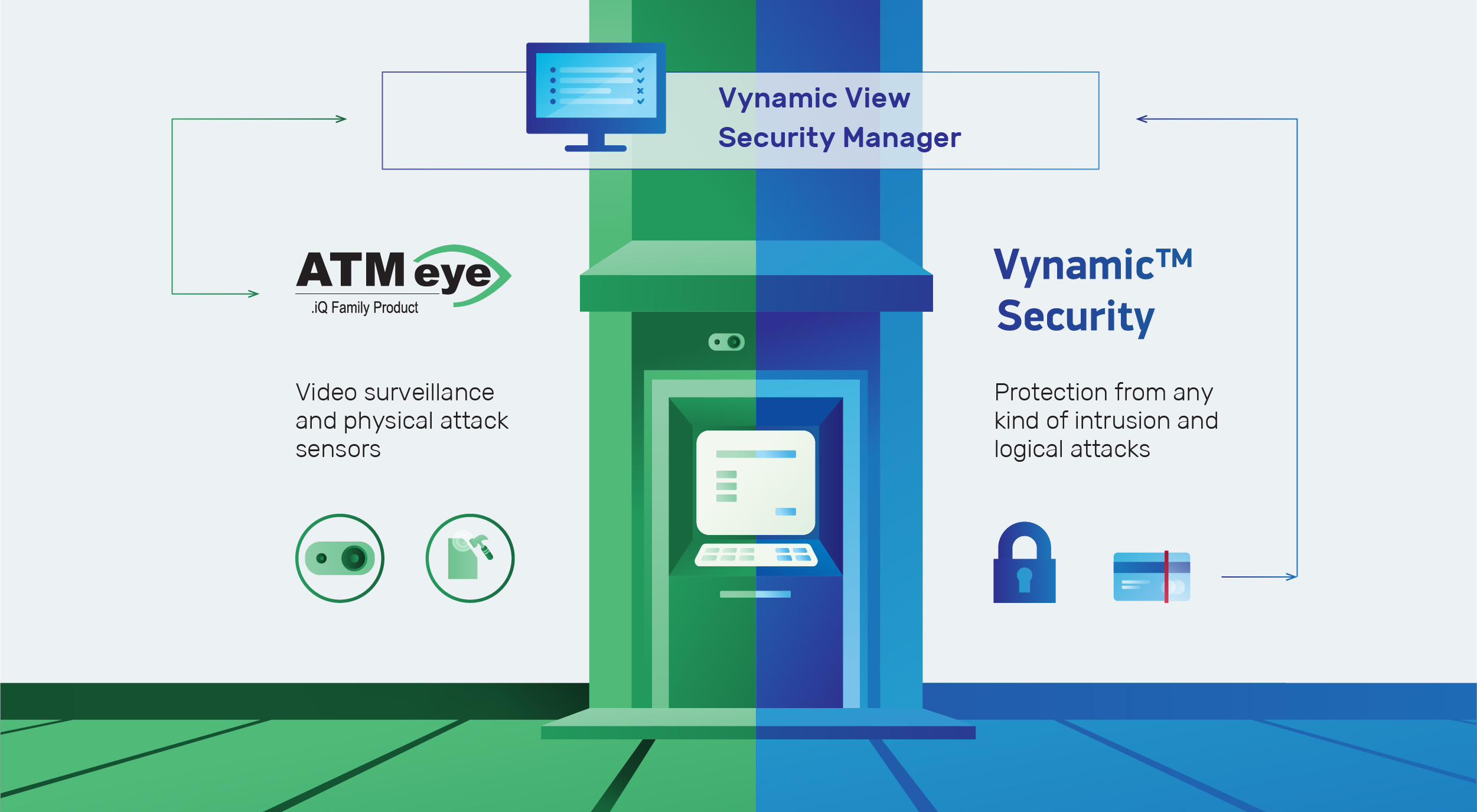
Contact our company representatives to learn more about ATMeye.iQ and Vynamic Security solutions.